My Mac is connected to the Internet 24-hours a day and whether I’m using it, or not, data is continually exchanged between my Mac and servers located elsewhere. Many applications that I use on the Mac send or receive data.
Take a look at all the processes running in the Network tab of Activity Monitor application. There are numerous processes and understanding them is a huge pain.
To understand what is going on, an application can help. Little Snitch is an advanced, host-based application firewall for Mac. It provides detailed firewalling and reports on processes, outgoing and incoming connection, ports and protocol along with detailed traffic history down to one minute resolution.
In this tutorial, I’ll show you how to use Little Snitch:
- To allow or deny a network connection
- To monitor and record network activity
- To take a snapshot of the network activity
- To create profiles for different network conditions
- To manage all the rules created in the dashboard
Using Little Snitch
The Mac includes a built-in firewall that’s expressly designed to be as simple as possible. It is based on applications—you can specify, for each app, whether to allow or block incoming connections.
This makes it easier to gain the benefits of firewall protection, and helps prevent undesirable apps from taking control of network ports open for legitimate apps.
While OS X application level firewall is great at putting on a good defence, monitoring the outbound traffic can be enlightening and possibly a little disturbing.
Little Snitch monitors outbound traffic instead of, or in addition to, incoming traffic. The main reason is to make you aware of—and enable you to block applications that might be invisibly sending out personal information in the background.
Plenty of software connects to the internet without any visible interface or notification. For example—email applications downloading messages in the background, an application checking for software updates periodically, Dropbox syncing newly changed files, and so on.
These activities are fine, but if you download an application that secretly logs keystrokes and sends sensitive data somewhere, then it’s a problem. Little Snitch can help you track malicious applications.
Some software phones home to validate registration data. Some software may collects and sends personally identifiable data without your consent. It may also sniff or broadcast over the network details of the computer and even how you use an application. Little Snitch‘s network monitor can help you to track those applications that frequently phone home.
Many of us now work from different places. This, in turn, means different networks in places such as an Internet cafe, coffee shop, shared workspace or even over a mobile network.
Firewalls are an important aspect of computer security. If you’re connected to a public network, you might want to forbid certain incoming connections. If the Mac is connected to the mobile network then the data usage may be the primary concern.
Little Snitch groups these rules into profiles that can be network-specific or global. It can switch profiles automatically when particular networks are joined.
Allow or Deny a Network Connection
When Little Snitch encounters a connection attempt, it shows a connection alert window. This lets you decide whether to allow or deny the connection and simultaneously create a rule declaring how to handle future, similar connections.
There are four aspects to consider:
1. Connection Summary
The Connection Summary provides a brief description of the connection attempt, including the names of involved processes and servers as well as protocol and port information. If an application uses a helper tool to establish the connection, the name of this tool is shown next to the application name. For example—Safari via WebProcess.
Click the Show Details button to get a comprehensive list of connection details such as Process ID, Process Owner, IP address, reverse DNS name and more.
Click the Hide Details button to hide all the information.

2. Rule Options
To prevent the connection alert from being shown again for similar connections from the same process, you can create a rule declaring how to handle those future connection attempts. You can choose from one of these rule options to define how specific the rule shall be:
- Any connection—The rule matches any future connection attempt for this process
- Only port—The rule matches only for connections to the same port. In this case you want to allow iTunes only through port 443, for example
- Only server—The rule matches only for connections with the same remote server. In this case you want to allow iTunes only through itunes.apple.com
- Only server and port—The rule matches only for connections with the same remote server and the same port
The port specific rule options—Only port, Only server and port—are only visible if the detail level is configured to show port details.
To configure detail level click Open Little Snitch Preferences in the menu bar, go to Alert tab and select Show Full Details. The more details you hide, the simpler becomes the connection alert and the fewer options you’ll have.
It’s much easier, and quicker, to find the most frequently used options in a simple alert.

3. Rule Lifetime
The Rule Lifetime lets you specify whether the connection shall be allowed or denied permanently or temporarily. Select one of the temporary options from the pop-up menu according to your criteria.
- Until Quit—The rule expires when the process terminates
- Until Logout—The rule expires when the user logs out
- Until Restart—The rule expires when the computer is restarted
- Lifetime in Minutes—The rule expires after a certain period of time
- Once—The connection is allowed or denied exactly once. No rule is created and as soon as another connection is attempted, Little Snitch shows a new connection alert

4. Rule Action
This is the final step in Little Snitch for creating a rule. Click the Allow button to allow the connection or else click the Deny button to deny the connection.
If no rule matches then Little Snitch may ask the user what to do.

Monitor and Record the Network Activity
Little Snitch Network Monitor complements Little Snitch’s rule based network filter. It performs a number of useful functions:
- Checks whether the filter rules perform as you had planned
- If a application does not work as expected and you suspect that it interferes with a deny-rule
- If you are concerned that a process has just connected to the Internet although it should not
There are three main components of network monitor—Connection List, Traffic Diagram, and Connection Inspector.
These options are controlled through Network Monitor Menu. This lets you change filtering and sorting options, manage snapshots, and open Preferences.
You can open the Connection Inspector for details about the selected connection and toggle the visibility of Traffic Diagram.
1. Connection List
The Connection List is the primary window of Little Snitch‘s Network Monitor.
The Server Column shows the name of the server with the most recent activity. If a server has multiple names, hover the name with the mouse to see all the alternative names.
Servers in red are blocked because their connections were denied. Servers in white are currently connected. If the process did connect to more than one server, the number of additional connections is shown next to the hostname. Click the number to reveal these additional connections.

Traffic Meters display the current traffic rate of a process. Green bars represent the download activity while red bar represent the upload activity.
If you select the Sort by Traffic Amounts option from the Network Monitor menu, the traffic meters are replaced with bars displaying total traffic data, in red and green, for upload and download activity.
The list of connections can be limited to connections with recent activity.
Click Show only Last from the pop-menu and select a time limit. By default, all connections generated from the local network are suppressed because they generate a lot of activity, but if you are troubleshooting a problem in the local network, e.g. a network printer, choose Show Local Network in the pop-up menu.
The connection list can be searched for different properties of connection. You can search for process, hostname, IP Address, Protocol, Port, and Status.
Click on the search field’s menu to see the list of properties that can be searched. For example—if an application behaves in an unexpected way and you suspect that a deny-rule might cause the problem, search for status:denied and inspect recently denied connections.

2. Traffic Diagram
The traffic diagram provides a graphical representation of the Mac’s recent network activity. You can view and analyse total traffic amounts, peak and average traffic rates, and system related events such as the launch or termination of applications.
Hover the cursor over the traffic diagram with mouse to get an overlay pop-up with download and upload rates from any point in time. The Total Amounts display shows the total amount of received and sent data within the selected range. Hold down the Option key to see average data rates …averaged over the entire selection.
The Zoom slider selects a zoom level down to one minute. From the gear wheel menu in the bottom left corner, choose between linear and logarithmic data rate display, turn auto-zoom on/off and zoom presets.
System events such as launch or termination of applications are marked with yellow diamonds. Hover the cursor over them to see a description of the event.
Select a time range in the traffic diagram and the connection list focuses on connections that actually had any traffic during that time. If you see a traffic peak in the diagram, you can select it to see which process caused it.
The selected time range can be moved freely by holding down the Command key and dragging it with the mouse. All the data in traffic diagram are updated in real-time.

3. Connection Inspector
The Connection Inspector shows all the technical details recorded for a connection or summary of connections. Select a connection and click i in the network monitor menu to open the inspector.
The details shown are—the file system path of the process, reverse DNS lookup names if available, all IP addresses, and detailed connection statistics such as protocol, port, total traffic the connection sent or received, last activity, and more.

Take a Snapshot of the Network Activity
Sometimes you want to preserve something for the future. You might have found an issue with the network and want to share the details with the ISP, or you just want to take some time to analyse the network traffic data without fear that information might be lost.
Little Snitch Network Monitor can make snapshots of the history currently stored, and the connection list built from this history.
Choose Make Snapshot from the Network Monitor menu or press Command-D while the connection list window is in front. This duplicates the current status of the connection list. View the data in the connection list and sort by either traffic amounts or last activity, and view the technical details recorded for a connection.

If you want to share the snapshot with an ISP you might first want to delete some connections from snapshot. Right-click any rule and choose Delete from List to delete the connection. Alternatively, you can save a snapshot directly to the disk with the menu option Save Snapshot or Command-S.
Note that some things are displayed differently in snapshots than in real-time views. Relative dates are given with respect to the snapshot date and the connected/disconnected status is not available.

Create Profiles for Different Network Conditions
Profiles are a means to switch between rule sets easily. When rules are matched against a connection attempt, all rules in the current profile are considered first. The importance of this simple concept are manifold.
- If you are in a public network e.g. an Internet Cafe, you might want to forbid incoming connections from everywhere to all the handy sharing services
- If the Mac is connected to the mobile network then the data usage can be a primary concern. It’s not the best idea to download updates, download music or perform an online backup while you’re in one of these networks. Little Snitch can deny Internet access for all these services
- If you’re giving presentation on a projector, you probably don’t want any connection alert to interrupt. Little Snitch silent mode blocks alerts temporarily
Automatic Profile Switching allows you to associate different networks—Wi-Fi at home, public hotspot, LTE—with certain profiles in Little Snitch.
Whenever you join one of these networks, Little Snitch detects the network change and switches to the associated profile automatically. This allows you to apply different rule sets depending on the network you’re connected to.
Automatic Profile Switching is disabled by default.
To enable it, go to Little Snitch Configuration > Preferences > Automatic Profile Switching. When joining an unknown network that you haven’t joined before, you can choose profile switching alert to show the pop-window every time you connect to an unknown network.
You can also active a certain profile when an unknown network is joined. If you travel a lot, and join many different network it is advisable to create a different profile so you don’t have to fiddle with rules every time.

When joining an unknown network, Little Snitch pauses all network traffic. The Profile Switching Alert appears and only after you have dealt with it is network traffic resumed.
You can review and edit the mappings between profiles and networks in the profiles section of the sidebar in Little Snitch Configuration.
Click the small button next to the profile, that have any networks assigned to them. A pop-over window will open to list all the networks that are currently mapped to this profile.

Manage All Rules in Dashboard
Little Snitch Configuration is the interface for managing rules and profiles. It’s also the central hub for editing preferences of all the components of Little Snitch. The interface is divided into three sections:
1. Sidebar
The sidebar provides convenient access to Rules, Suggestions, and Profiles. The Rules section contains various smart filters focussing on different types of rules:
-
Protected Rules—part of the factory rule set and crucial for the system to work properly and hence cannot be deleted. They are tagged with lock icon for visual identification
-
Unapproved Rules—By default, rules created with the alert window are auto approved. In the preferences section Advanced, rules created from the connection alert can also be set to unapproved, just uncheck Approve Rules Automatically. To approve a rule, right-click and choose Approve from the context menu
-
System Rules—This section only shows those rules that are restricted to system processes. Typically, these are system wide services running permanently in background. They are tagged with gear icon for visual identification
-
Background Processes—This section only shows those rules that are related to background processes without any windows or other graphical user interface, in contrast to GUI Applications
-
Global Rules—shows those rules that are not restricted to a particular process owner, but are effective for any user
-
Temporary Rules—Temporary rules have a limited lifetime and expire at a certain point in time, e.g. when the corresponding application quits
While Rules define how traffic should be filtered, Suggestions have no effect on the network filter. Rule suggestions have the same set of properties as rules, but they usually don’t have any action. They can be converted into rules easily. Rule suggestions are created in following conditions:
- When a connection is allowed or denied automatically. This happens when Little Snitch is running in Silent Mode
- When no rule matches and no connection alert can be shown. This happens when no user is logged in or an application is running in full screen
- When a rule gets expired or invalid. This happens when you create a temporary rule for any application or delete the application from the Mac
- Redundant rules have no effect because they are overruled by another rule with higher precedence. These rules can safely be deleted, unless you plan to delete or disable the overriding rule
In addition to rules filtering, you can also manage profiles in the sidebar. Drag a rule on a profile to make it effective in only that profile. If an existing rule matches almost exactly what you want, that rule can duplicated.
You don’t have to create new rules for every profile, since every rule can be duplicated. To duplicate one or more selected rules, secondary-click on the selected rules and choose Duplicate from the context menu.

2. Rules List
The middle portion of Little Snitch Configuration consists of list of rules. These rules define how network traffic is filtered. Whenever you manually create, modify or duplicate a rule, the rule editor will be opened. Rule editor is used to create new rules or edit existing ones.
To create a new rule, click + in the main window’s bottom bar or New in the toolbar. To edit an existing rule, double-click it. The rule editor is responsible for editing the rule’s action and properties.
You can set actions to Allow connections, Deny connections, or Ask and match their properties related to process.
Click the application icon for options related to the process, e.g. choose application, iOS Simulator Application. The process owner can be Me, System, or Anyone. At last set the properties related to the remote server, you can change port, protocol, and remote server address in this section.
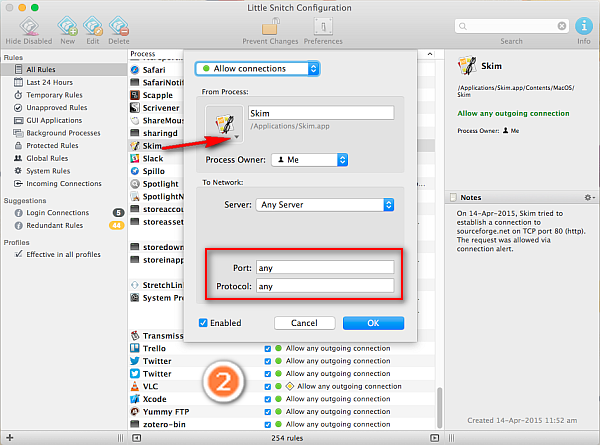
3. Info Pane
This part of the window contains all the detail information about the currently selected rule or suggestion. It displays the date and time when a rule was created and basic comment describing their purpose.
Rules created from a connection alert contain the information presented in the connection alert in their notes. The remote server this application is connecting to, port and protocol details, and more. You can edit the notes at any time.

Conclusion
Little Snitch is a powerful, advanced, host-based application firewall for Mac. Most of the firewall applications, including Little Snitch will constantly pop-up alerts about outgoing connection.
In this tutorial, I have shown you how to use Little Snitch to allow or deny a network connection, to monitor and record network activity, create snapshots of the network activity, create profiles for different network conditions, and manage all the rules in the dashboard.
{excerpt}
Read More