We drank chilled beverage after chilled beverage to bring you the best coolers and ice chests for every situation.
Category: Tech news
hacking,system security,protection against hackers,tech-news,gadgets,gaming
To Help Migrants at the Border, Aid Groups Deploy Tech
An immigrant support group builds a secure digital locker to store documents, as aid organizations rig solutions to provide cell signals.
Fractal Patterns Offer Clues to the Universe’s Origin
A new look at a ubiquitous phenomenon has uncovered unexpected fractal behavior that could help explain the birth of the universe and the arrow of time.
Hackers Could Decrypt Your GSM Phone Calls
Researchers have discovered a flaw in the GSM standard used by AT&T and T-Mobile that would allow hackers to listen in.
A Remote-Start App Exposed Thousands of Cars to Hackers
The bugs could have let an industrious hacker locate cars, unlock them, and start them up from anywhere with an internet connection.
How safe are school records? Not very, says student security researcher
If you can’t trust your bank, government or your medical provider to protect your data, what makes you think students are any safer?
Turns out, according to one student security researcher, they’re not.
Eighteen-year-old Bill Demirkapi, a recent high school graduate in Boston, Massachusetts, spent much of his latter school years with an eye on his own student data. Through self-taught pen testing and bug hunting, Demirkapi found several vulnerabilities in a his school’s learning management system, Blackboard, and his school district’s student information system, known as Aspen and built by Follett, which centralizes student data, including performance, grades, and health records.
The former student reported the flaws and revealed his findings at the Def Con security conference on Friday.
“I’ve always been fascinated with the idea of hacking,” Demirkapi told TechCrunch prior to his talk. “I started researching but I learned by doing,” he said.
Among one of the more damaging issues Demirkapi found in Follett’s student information system was an improper access control vulnerability, which if exploited could have allowed an attacker to read and write to the central Aspen database and obtain any student’s data.
Blackboard’s Community Engagement platform had several vulnerabilities, including an information disclosure bug. A debugging misconfiguration allowed him to discover two subdomains, which spat back the credentials for Apple app provisioning accounts for dozens of school districts, as well as the database credentials for most if not every Blackboard’s Community Engagement platform, said Demirkapi.
“School data or student data should be taken as seriously as health data. The next generation should be one of our number one priorities, who looks out for those who can’t defend themselves.”
Bill Demirkapi, security researcher
Another set of vulnerabilities could have allowed an authorized user — like a student — to carry out SQL injection attacks. Demirkapi said six databases could be tricked into disclosing data by injecting SQL commands, including grades, school attendance data, punishment history, library balances, and other sensitive and private data.
Some of the SQL injection flaws were blind attacks, meaning dumping the entire database would have been more difficult but not impossible.
In all, over 5,000 schools and over five million students and teachers were impacted by the SQL injection vulnerabilities alone, he said.
Demirkapi said he was mindful to not access any student records other than his own. But he warned that any low-skilled attacker could have done considerable damage by accessing and obtaining student records, not least thanks to the simplicity of the database’s password. He wouldn’t say what it was, only that it was “worse than ‘1234’.”
But finding the vulnerabilities was only one part of the challenge. Disclosing them to the companies turned out to be just as tricky.
Demirkapi admitted that his disclosure with Follett could have been better. He found that one of the bugs gave him improper access to create his own “group resource,” such as a snippet of text, which was viewable to every user on the system.
“What does an immature 11th grader do when you hand him a very, very, loud megaphone?” he said. “Yell into it.”
And that’s exactly what he did. He sent out a message to every user, displaying each user’s login cookies on their screen. “No worries, I didn’t steal them,” the alert read.
“The school wasn’t thrilled with it,” he said. “Fortunately, I got off with a two-day suspension.”
He conceded it wasn’t one of his smartest ideas. He wanted to show his proof-of-concept but was unable to contact Follett with details of the vulnerability. He later went through his school, which set up a meeting, and disclosed the bugs to the company.
Blackboard, however, ignored Demirkapi’s responses for several months, he said. He knows because after the first month of being ignored, he included an email tracker, allowing him to see how often the email was opened — which turned out to be several times in the first few hours after sending. And yet the company still did not respond to the researcher’s bug report.
Blackboard eventually fixed the vulnerabilities, but Demirkapi said he found that the companies “weren’t really prepared to handle vulnerability reports,” despite Blackboard ostensibly having a published vulnerability disclosure process.
“It surprised me how insecure student data is,” he said. “School data or student data should be taken as seriously as health data,” he said. “The next generation should be one of our number one priorities, who looks out for those who can’t defend themselves.”
He said if a teenager had discovered serious security flaws, it was likely that more advanced attackers could do far more damage.
Heather Phillips, a spokesperson for Blackboard, said the company appreciated Demirkapi’s disclosure.
“We have addressed several issues that were brought to our attention by Mr. Demirkapi and have no indication that these vulnerabilities were exploited or that any clients’ personal information was accessed by Mr. Demirkapi or any other unauthorized party,” the statement said. “One of the lessons learned from this particular exchange is that we could improve how we communicate with security researchers who bring these issues to our attention.”
Follet spokesperson Tom Kline said the company “developed and deployed a patch to address the web vulnerability” in July 2018.
The student researcher said he was not deterred by the issues he faced with disclosure.
“I’m 100% set already on doing computer security as a career,” he said. “Just because some vendors aren’t the best examples of good responsible disclosure or have a good security program doesn’t mean they’re representative of the entire security field.”
How a Swedish saxophonist built Kobalt, the world’s next music unicorn
You may not have heard of Kobalt before, but you probably engage with the music it oversees every day, if not almost every hour. Combining a technology platform to better track ownership rights and royalties of songs with a new approach to representing musicians in their careers, Kobalt has risen from the ashes of the 2000 dot-com bubble to become a major player in the streaming music era. It is the leading alternative to incumbent music publishers (who represent songwriters) and is building a new model record label for the growing “middle class’ of musicians around the world who are stars within niche audiences.
Having predicted music’s digital upheaval early, Kobalt has taken off as streaming music has gone mainstream across the US, Europe, and East Asia. In the final quarter of last year, it represented the artists behind 38 of the top 100 songs on U.S. radio.
Along the way, it has secured more than $200 million in venture funding from investors like GV, Balderton, and Michael Dell, and its valuation was last pegged at $800 million. It confirmed in April that it is raising another $100 million to boot. Kobalt Music Group now employs over 700 people in 14 offices, and GV partner Avid Larizadeh Duggan even left her firm to become Kobalt’s COO.
How did a Swedish saxophonist from the 1980s transform into a leading entrepreneur in music’s digital transformation? Why are top technology VCs pouring money into a company that represents a roster of musicians? And how has the rise of music streaming created an opening for Kobalt to architect a new approach to the way the industry works?
Gaining an understanding of Kobalt and its future prospects is a vehicle for understanding the massive change underway across the global music industry right now and the opportunities that is and isn’t creating for entrepreneurs.
This article is Part 1 of the Kobalt EC-1, focused on the company’s origin story and growth. Part 2 will look at the company’s journey to create a new model for representing songwriters and tracking their ownership interests through the complex world of music royalties. Part 3 will look at Kobalt’s thesis about the rise of a massive new middle class of popular musicians and the record label alternative it is scaling to serve them.
Table of Contents
- Early lessons on the tough road of entrepreneurship
- From band leader to music label founder
- Leaving music behind… but not for long
- So what exactly is Kobalt?
- The wind (finally) in Kobalt’s sails: music is booming again
- What Kobalt is today
- How I’ll assess Kobalt over the next two posts
Early lessons on the tough road of entrepreneurship
It’s tough to imagine a worse year to launch a music company than 2000. Willard Ahdritz, a Swede living in London, left his corporate consulting job and sold his home for £200,000 to fully commit to his idea of a startup collecting royalties for musicians. In hindsight, his timing was less than impeccable: he launched Kobalt just as Napster and music piracy exploded onto the mainstream and mere months before the dot-com crash would wipe out much of the technology industry.
The situation was dire, and even his main seed investor told him he was doomed once the market crashed. “Eating an egg and ham sandwich…have you heard this saying? The chicken is contributing but the pig is committed,” Ahdritz said when we first spoke this past April (he has an endless supply of sayings). “I believe in that — to lose is not an option.”
Entrepreneurial hardship though is something that Ahdritz had early experience with. Born in Örebro, a city of 100,000 people in the middle of Sweden, Ahdritz spent a lot of time as a kid playing in the woods, which also holding dual interests in music and engineering. The intersection of those two converged in the synthesizer revolution of early electronic music, and he was fascinated by bands like Kraftwerk.
Adobe’s Amit Ahuja will be talking customer experience at TechCrunch Sessions: Enterprise
As companies collect increasingly large amounts of data about customers, the end game is about improving the customer experience. It’s a term we’re hearing a lot of these days, and we are going to be discussing that very topic with Amit Ahuja, Adobe’s vice president of ecosystem development, next month at TechCrunch Sessions: Enterprise in San Francisco. Grab your early-bird tickets right now — $100 savings ends today!
Customer experience covers a broad array of enterprise software and includes data collection, analytics and software. Adobe deals with all of this, including the Adobe Experience Platform for data collection, Adobe Analytics for visualization and understanding and Adobe Experience Cloud for building applications.
The idea is to begin to build an understanding of your customers through the various interactions you have with them, and then build applications to give them a positive experience. There is a lot of talk about “delighting” customers, but it’s really about using the digital realm to help them achieve what they want as efficiently as possible, whatever that means to your business.
Ahuja will be joining TechCrunch’s editors, along with Qualtrics chief experience officer Julie Larson-Green and Segment CEO Peter Reinhardt to discuss the finer points of what it means to build a customer experience, and how software can help drive that.
Ahuja has been with Adobe since 2005 when he joined as part of the $3.4 billion Macromedia acquisition. His primary role today involves building and managing strategic partnerships and initiatives. Prior to this, he was the head of Emerging Businesses and the GM of Adobe’s Data Management Platform business, which focuses on advertisers. He also spent seven years in Adobe’s Corporate Development Group, where he helped complete the acquisitions of Omniture, Scene7, Efficient Frontier, Demdex and Auditude.
Amit will be joining us on September 5 in San Francisco, along with some of the biggest influencers in enterprise, including Bill McDermott from SAP, Scott Farquhar from Atlassian, Aparna Sinha from Google, Wendy Nather from Duo Security, Aaron Levie from Box and Andrew Ng from Landing AI.
Early-bird savings end today, August 9. Book your tickets today and you’ll save $100 before prices go up.
Bringing a group? Book our 4+ group tickets and you’ll save 20% on the early-bird rate. Bring the whole squad here.
Biotech researchers venture into the wild to start their own business
Contributor
Much of Silicon Valley mythology is centered on the founder-as-hero narrative. But historically, scientific founders leading the charge for bio companies have been far less common.
Developing new drugs is slow, risky and expensive. Big clinical failures are all too common. As such, bio requires incredibly specialized knowledge and experience. But at the same time, the potential for value creation is enormous today more than ever with breakthrough new medicines like engineered cell, gene and digital therapies.
What these breakthroughs are bringing along with them are entirely new models — of founders, of company creation, of the businesses themselves — that will require scientists, entrepreneurs and investors to reimagine and reinvent how they create bio companies.
In the past, biotech VC firms handled this combination of specialized knowledge + binary risk + outsized opportunity with a unique “company creation” model. In this model, there are scientific founders, yes; but the VC firm essentially founded and built the company itself — all the way from matching a scientific advance with an unmet medical need, to licensing IP, to having partners take on key roles such as CEO in the early stages, to then recruiting a seasoned management team to execute on the vision.
Image: PASIEKA/SCIENCE PHOTO LIBRARY/Getty Images
You could call this the startup equivalent of being born and bred in captivity — where great care and feeding early in life helps ensure that the company is able to thrive. Here the scientific founders tend to play more of an advisory role (usually keeping day jobs in academia to create new knowledge and frontiers), while experienced “drug hunters” operate the machinery of bringing new discoveries to the patient’s bedside. This model’s core purpose is to bring the right expertise to the table to de-risk these incredibly challenging enterprises — nobody is born knowing how to make a medicine.
But the ecosystem this model evolved from is evolving itself. Emerging fields like computational biology and biological engineering have created a new breed of founder, native to biology, engineering and computer science, that are already, by definition, the leading experts in their fledgling fields. Their advances are helping change the industry, shifting drug discovery away from a highly bespoke process — where little knowledge carries over from the success or failure of one drug to the next — to a more iterative, building-block approach like engineering.
Take gene therapy: once we learn how to deliver a gene to a specific cell in a given disease, it is significantly more likely we will be able to deliver a different gene to a different cell for another disease. Which means there’s an opportunity not only for novel therapies but also the potential for new business models. Imagine a company that provides gene delivery capability to an entire industry — GaaS: gene-delivery as a service!
Once a founder has an idea, the costs of testing it out have changed too. The days of having to set up an entire lab before you could run your first experiments are gone. In the same way that AWS made starting a tech company vastly faster and easier, innovations like shared lab spaces and wetlab accelerators have dramatically reduced the cost and speed required to get a bio startup off the ground. Today it costs thousands, not millions, for a “killer experiment” that will give a founding team (and investors) early conviction.
What all this amounts to is scientific founders now have the option of launching bio companies without relying on VCs to create them on their behalf. And many are. The new generation of bio companies being launched by these founders are more akin to being born in the wild. It isn’t easy; in fact, it’s a jungle out there, so you need to make mistakes, learn quickly, hone your instincts, and be well-equipped for survival. On the other hand, given the transformative potential of engineering-based bio platforms, the cubs that do survive can grow into lions.

Image via Getty Images / KTSDESIGN/SCIENCE PHOTO LIBRARY
So, which is better for a bio startup today: to be born in the wild — with all the risk and reward that entails — or to be raised in captivity
The “bred in captivity” model promises sureness, safety, security. A VC-created bio company has cache and credibility right off the bat. Launch capital is essentially guaranteed. It attracts all-star scientists, executives and advisors — drawn by the balance of an innovative, agile environment and a well-funded, well-connected support network. I was fortunate enough to be an early executive in one of these companies, giving me the opportunity to work alongside industry luminaries and benefit from their well-versed knowledge of how to build a world-class bio company with all its complex component parts: basic, translational, clinical research, from scratch. But this all comes at a price.
Because it’s a heavy lift for the VCs, scientific founders are usually left with a relatively small slug of equity — even founding CEOs can end up with ~5% ownership. While these companies often launch with headline-grabbing funding rounds of $50m or above, the capital is tranched — meaning money is doled out as planned milestones are achieved. But the problem is, things rarely go according to plan. Tranched capital can be a safety net, but you can get tangled in that net if you miss a milestone.
Being born in the wild, on the other hand, trades safety for freedom. No one is building the company on your behalf; you’re in charge, and you bear the risk. As a recent graduate, I co-founded a company with Harvard geneticist George Church. The company was bootstrapped — a funding strategy that was more famine than feast — but we were at liberty to try new things and run (un)controlled experiments like sequencing heavy metal wildman Ozzy Osbourne.

It was the early, Wild West days of the genomics revolution and many of the earliest biotech companies mirrored that experience — they weren’t incepted by VCs; they were created by scrappy entrepreneurs and scientists-turned-CEO. Take Joshua Boger, organic chemist and founder of Vertex Pharmaceuticals: starting in 1989 his efforts to will into existence a new way to develop drugs, thrillingly captured in Barry Werth’s The Billion-Dollar Molecule and its sequel The Antidote in all its warts and nail-biting glory, ultimately transformed how we treat HIV, hepatitis C and cystic fibrosis.
Today we’re in a back-to-the-future moment and the industry is being increasingly pushed forward by this new breed of scientist-entrepreneur. Students-turned-founder like Diego Rey of in vitro diagnostics company GeneWEAVE and Ramji Srinivasan of clinical laboratory Counsyl helped transform how we diagnose disease and each led their companies to successful acquisitions by larger rivals.
Popular accelerators like Y Combinator and IndieBio are filled with bio companies driven by this founder phenotype. Ginkgo Bioworks, the first bio company in Y Combinator and today a unicorn, was founded by Jason Kelly and three of his MIT biological engineering classmates, along with former MIT professor and synthetic biology legend Tom Knight. The company is not only innovating new ways to program biology in order to disrupt a broad range of industries, but it’s also pioneering an innovative conglomerate business model it has dubbed the “Berkshire for biotech.”
Like the Ginkgo founders, Alec Nielsen and Raja Srinivas launched their startup Asimov, an ambitious effort to program cells using genetic circuits, shortly after receiving their PhDs in biological engineering from MIT. And, like Boger, renowned machine learning Stanford professor Daphne Koller is working to once again transform drug discovery as the founder and CEO of Instiro.
Just like making a medicine, no one is born knowing how to build a company. But in this new world, these technical founders with deep domain expertise may even be more capable of traversing the idea maze than seasoned operators. Engineering-based platforms have the potential to create entirely new applications with unprecedented productivity, creating opportunities for new breakthroughs, novel business models, and new ways to build bio companies. The well-worn playbooks may be out of date.
Founders that choose to create their own companies still need investors to scrub in and contribute to the arduous labor of company-building — but via support, guidance, and with access to networks instead. And like this new generation of founders, bio investors today need to rethink (and re-value) the promise of the new, and still appreciate the hard-earned wisdom of the old. In other words, bio investors also need to be multidisciplinary. And they need to be comfortable with a different kind of risk: backing an unproven founder in a new, emerging space. As a founder, if you’re willing to take your chances in the wild, you should have an investor that understands you, believes in you, can support you and, importantly, is willing to dream big with you.
Car2go hikes hourly rental rates by as much as a third
By-the-minute car rental service Car2go is raising its rates for short trips under the guise of variable pricing, the company announced to its users today. As we’ve seen with other variably priced services like delivery and ride hailing, in practice this means you never really know what it will cost but will have little choice but to pay.
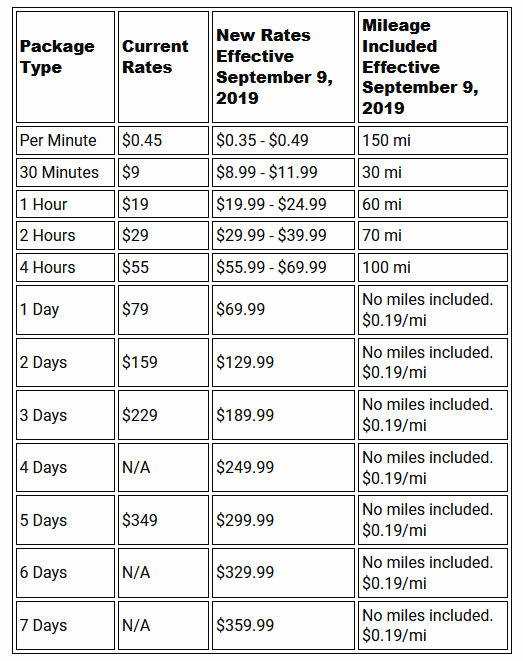
In an email to users of its service, Car2go said that as a result of “constantly evaluating our product, packages, and pricing strategies” it had arrived at the new system, under which price will depend on time, location and day. The new cost structure takes effect next month.
For Car2go users, this will generally mean paying more. The company highlighted a new cheaper possible per-minute rate of 35 cents, significantly lower than the current $0.45 rate. But it’s easy to guess when that lower rate will be available: “times, locations and days” that no one is using the service. Meanwhile, it’s also possible to encounter a new higher per-minute rate of up to 49 cents when cars are in demand or in a high-use location.
Blocks of time from half an hour to four hours are all increasing in price: The current flat rates are now floor rates, with the possibility you’ll be paying as much as a third more than before. For example, a two-hour block currently costs $29; soon it will cost somewhere between $30 and $39. Again, you won’t know until you open the app to check it out, at which point you’re probably already committed.
Day-length packages are actually cheaper under the new system, but no longer include miles, so while a 24-hour pass used to be $79, now it’s $70 — but at 19 cents per mile, you’ll be in the red after less than 50 miles. And the price only goes up from there. Still, it’s conceivable you’ll pay less for a two or three-day rental if you’re not actually going anywhere distant, but just need a car for the weekend.
A newly instituted zone-based charge and refund system punishes drivers for leaving the city center and rewards those at the periphery for driving back toward heavy usage areas. There’s a $5 charge if you leave the central zone, and $5 refund — or the price of the trip, if less — if you bring a car in from the outer one. (Consult your local Car2go to see what the zones are in your city.)
Count the cards here and you can see the house always wins. If you’re going out, the full $5 fee always applies. If you’re coming in, it will be very difficult to nail that $5 ride — go under and Car2go is reimbursing less than the $5 (and thus comes out ahead), go over and you end up paying money anyway. It’s just one of those clever little traps businesses set up.
You can see the full changes in the chart below:
 Oh, and your first 200 trips this calendar year have an additional $1 fee. You’re welcome!
Oh, and your first 200 trips this calendar year have an additional $1 fee. You’re welcome!
In case you can’t tell, this is bad news for consumers, though it would be too much to expect that these prices would stay stable for years. But variable pricing is fundamentally anti-consumer because of a lack of transparency under which the companies controlling it can pull all kinds of shenanigans. Sadly, that makes it a great choice for the bottom line.
These unwelcome changes come six months after Car2go joined the BMW-Daimler joint venture Share Now, which has a variety of car-share services around the world it intends to unify under a single brand soon (it already killed ReachNow, rather abruptly). Apparently larger scale and reduced competition don’t actually lead to lower prices — unfortunate for their customers. But overall the floating car-share services are an important one. Just not as cheap as they used to be.
Apple starts selling Mophie’s take on AirPower
There’s no shortage of AirPower knockoffs on the market. Many have been in the works since Apple took the wraps off its in-house version, positioned as more affordable alternatives. Since the company unceremoniously pulled the plug on the project, however, they’re the only game in town.
We reviewed a $99 one a while ago. It seemed fine, and Amazon is currently overloaded with even more affordable options. It’s probably unfair to lump Mophie in the knockoff category. The accessory maker produces pretty premium products at prices to match. And unlike the competition, it’s got the Apple seal of approval.
That means the company’s new 3-in-1 charging pad is most likely as close as you’re ever going to get to marching into an Apple Store and leaving with AirPower. Here’s the official description, per Mophie:
The 3-in-1 wireless charging pad conveniently charges iPhone, AirPods and Apple Watch from one central location. To ensure a seamless charging experience for all three devices, it features a dedicated cavity for AirPods, and an integrated charging stand for Apple Watch that holds it at the ideal angle for Nightstand Mode with an unobstructed view of the screen.
Sounds about right, right? The black charging pad operates similarly to most competitors, with designated slots for the three Apple products. That, after all, seems to be the source of the issues with the original AirPower product, making a pad that was capable of charging three different products with different charging needs.
At $140, it’s in line with the AirPower’s price. As stated above, you can get an alternative for much cheaper, but maybe there’s something in the peace of mind of getting the device from a trusted name like Mophie.
Reports say White House has drafted an order putting the FCC in charge of monitoring social media
The White House is contemplating issuing an executive order that would widen its attack on the operations of social media companies.
The White House has prepared an executive order called “Protecting Americans from Online Censorship” that would give the Federal Communications Commission oversight of how Facebook, Twitter and other tech companies monitor and manage their social networks, according to a CNN report.
Under the order, which has not yet been announced and could be revised, the FCC would be tasked with developing new regulations that would determine when and how social media companies filter posts, videos or articles on their platforms.
The draft order also calls for the Federal Trade Commission to take those new policies into account when investigating or filing lawsuits against technology companies, according to the CNN report.
Social media censorship has been a perennial talking point for President Donald Trump and his administration. In May, the White House set up a tip line for people to provide evidence of social media censorship and a systemic bias against conservative media.
In the executive order, the White House says it received more than 15,000 complaints about censorship by the technology platforms. The order also includes an offer to share the complaints with the Federal Trade Commission.
As part of the order, the Federal Trade Commission would be required to open a public complaint docket and coordinate with the Federal Communications Commission on investigations of how technology companies curate their platforms — and whether that curation is politically agnostic.
Under the proposed rule, any company whose monthly user base includes more than one-eighth of the U.S. population would be subject to oversight by the regulatory agencies. A roster of companies subject to the new scrutiny would include Facebook, Google, Instagram, Twitter, Snap and Pinterest .
At issue is how broadly or narrowly companies are protected under the Communications Decency Act, which was part of the Telecommunications Act of 1996. Social media companies use the Act to shield against liability for the posts, videos or articles that are uploaded from individual users or third parties.
The Trump administration aren’t the only politicians in Washington are focused on the laws that shield social media platforms from legal liability. House Speaker Nancy Pelosi took technology companies to task earlier this year in an interview with Recode.
The criticisms may come from different sides of the political spectrum, but their focus on the ways in which tech companies could use Section 230 of the Act is the same.
The White House’s executive order would ask the FCC to disqualify social media companies from immunity if they remove or limit the dissemination of posts without first notifying the user or third party that posted the material, or if the decision from the companies is deemed anti-competitive or unfair.
The FTC and FCC had not responded to a request for comment at the time of publication.
Hundreds of exposed Amazon cloud backups found leaking sensitive data
How safe are your secrets? If you used Amazon’s Elastic Block Storage snapshots, you might want to check your settings.
New research just presented at the Def Con security conference reveals how companies, startups and governments are inadvertently leaking their own files from the cloud.
You may have heard of exposed S3 buckets — those Amazon-hosted storage servers packed with customer data but often misconfigured and inadvertently set to “public” for anyone to access. But you may not have heard about exposed EBS snapshots, which poses as much, if not a greater, risk.
These elastic block storage (EBS) snapshots are the “keys to the kingdom,” said Ben Morris, a senior security analyst at cybersecurity firm Bishop Fox, in a call with TechCrunch ahead of his Def Con talk. EBS snapshots store all the data for cloud applications. “They have the secret keys to your applications and they have database access to your customers’ information,” he said.
“When you get rid of the hard disk for your computer, you know, you usually shredded or wipe it completely,” he said. “But these public EBS volumes are just left for anyone to take and start poking at.”
He said that all too often cloud admins don’t choose the correct configuration settings, leaving EBS snapshots inadvertently public and unencrypted. “That means anyone on the internet can download your hard disk and boot it up, attach it to a machine they control, and then start rifling through the disk to look for any kind of secrets,” he said.
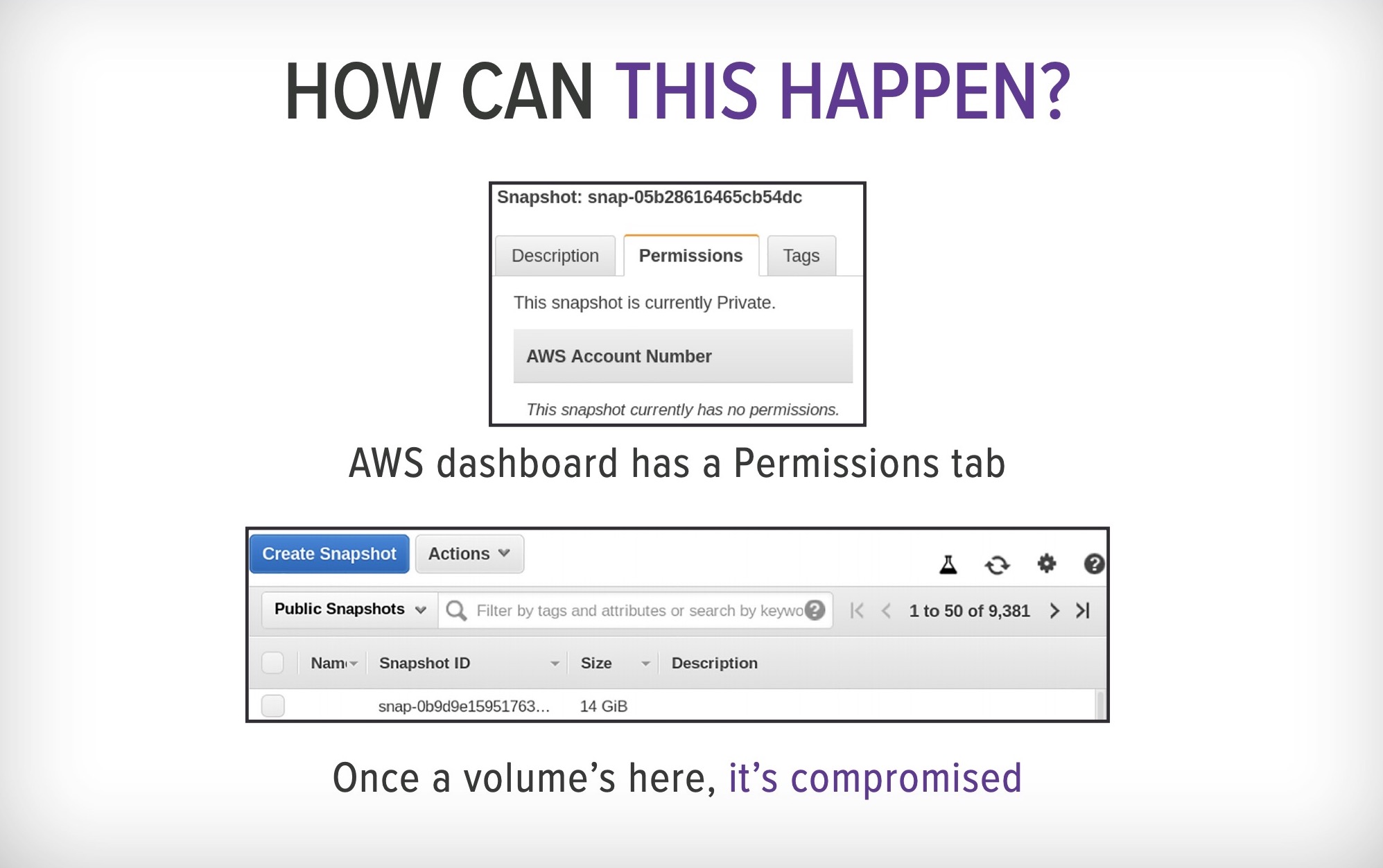
One of Morris’ Def Con slides explaining how EBS snapshots can be exposed. (Image: Ben Morris/Bishop Fox; supplied)
Morris built a tool using Amazon’s own internal search feature to query and scrape publicly exposed EBS snapshots, then attach it, make a copy and list the contents of the volume on his system.
“If you expose the disk for even just a couple of minutes, our system will pick it up and make a copy of it,” he said.

Another slide noting the types of compromised data found using his research, often known as the “Wall of Sheep” (Image: Ben Morris/Bishop Fox; supplied)
It took him two months to build up a database of exposed data and just a few hundred dollars spent on Amazon cloud resources. Once he validates each snapshot, he deletes the data.
Morris found dozens of snapshots exposed publicly in one region alone, he said, including application keys, critical user or administrative credentials, source code and more. He found several major companies, including healthcare providers and tech companies.
He also found VPN configurations, which he said could allow him to tunnel into a corporate network. Morris said he did not use any credentials or sensitive data, as it would be unlawful.
Among the most damaging things he found, Morris said he found a snapshot for one government contractor, which he did not name, but provided data storage services to federal agencies. “On their website, they brag about holding this data,” he said, referring to collected intelligence from messages sent to and from the so-called Islamic State terror group to data on border crossings.
“Those are the kind of things I would definitely not want to be exposed to the public internet,” he said.
He estimates the figure could be as many as 1,250 exposures across all Amazon cloud regions.
Morris plans to release his proof-of-concept code in the coming weeks.
“I’m giving companies a couple of weeks to go through their own disks and make sure that they don’t have any accidental exposures,” he said.
Daily Crunch: Uber reports big losses and slowing growth
The Daily Crunch is TechCrunch’s roundup of our biggest and most important stories. If you’d like to get this delivered to your inbox every day at around 9am Pacific, you can subscribe here.
1. Uber lost more than $5B last quarter
Uber reported earnings for the second time as a public company, posting its largest-ever quarterly loss. And while revenue grew 14% year-over-year, that also sparked concerns over (relatively) slow growth.
The company’s stock took a nose-dive of 11% in after-hours trading following the news.
2. HarmonyOS is Huawei’s Android alternative for smartphones and smart home devices
After months of conflicting statements from executives, Huawei has officially unveiled HarmonyOS, a distributed operating system developed to power smartphones, laptops and smart home devices as the company attempts to reduce its reliance on American firms.
3. Apple expands its bug bounty, increases maximum payout to $1M
Apple is finally giving security researchers something they’ve wanted for years: a macOS bug bounty.

Hustle and bustle of Indian roads around monument of Charminar in Hyderabad, India.
4. India’s Lendingkart raises $30M to help small businesses access working capital
Lendingkart Finance has issued over 60,000 loans to more than 55,000 small and medium-sized enterprises in 1,300 cities across India. The startup says it will use the fresh capital to widen its lending range and find new clients.
5. This startup is helping food app delivery workers start their own damn delivery companies
Dumpling’s goal is to turn today’s delivery workers into “solopreneurs” who build their own book of clients and keep much more of the money.
6. The smartwatch category is growing, as Apple remains dominant
The good news for smartwatches is that the category continues to grow — but the numbers start to look less rosy when you take Apple out of the equation. (Extra Crunch membership required.)
7. Quantum computing is coming to TC Sessions: Enterprise on Sept. 5
Joining us onstage will be Microsoft’s Krysta Svore, who leads the company’s quantum efforts; IBM’s Jay Gambetta, the principal theoretical scientist behind IBM’s quantum computing effort; and Jim Clarke, the director of quantum hardware at Intel Labs.
Why AI needs more social workers, with Columbia University’s Desmond Patton
Sometimes it does seem the entire tech industry could use someone to talk to, like a good therapist or social worker. That might sound like an insult, but I mean it mostly earnestly: I am a chaplain who has spent 15 years talking with students, faculty, and other leaders at Harvard (and more recently MIT as well), mostly nonreligious and skeptical people like me, about their struggles to figure out what it means to build a meaningful career and a satisfying life, in a world full of insecurity, instability, and divisiveness of every kind.
In related news, I recently took a year-long paid sabbatical from my work at Harvard and MIT, to spend 2019-20 investigating the ethics of technology and business (including by writing this column at TechCrunch). I doubt it will shock you to hear I’ve encountered a lot of amoral behavior in tech, thus far.
A less expected and perhaps more profound finding, however, has been what the introspective founder Prayag Narula of LeadGenius tweeted at me recently: that behind the hubris and Machiavellianism one can find in tech companies is a constant struggle with anxiety and an abiding feeling of inadequacy among tech leaders.
In tech, just like at places like Harvard and MIT, people are stressed. They’re hurting, whether or not they even realize it.
So when Harvard’s Berkman Klein Center for Internet and Society recently posted an article whose headline began, “Why AI Needs Social Workers…”… it caught my eye.
The article, it turns out, was written by Columbia University Professor Desmond Patton. Patton is a Public Interest Technologist and pioneer in the use of social media and artificial intelligence in the study of gun violence. The founding Director of Columbia’s SAFElab and Associate Professor of Social Work, Sociology and Data Science at Columbia University.
A trained social worker and decorated social work scholar, Patton has also become a big name in AI circles in recent years. If Big Tech ever decided to hire a Chief Social Work Officer, he’d be a sought-after candidate.
It further turns out that Patton’s expertise — in online violence & its relationship to violent acts in the real world — has been all too “hot” a topic this past week, with mass murderers in both El Paso, Texas and Dayton, Ohio having been deeply immersed in online worlds of hatred which seemingly helped lead to their violent acts.
Fortunately, we have Patton to help us understand all of these issues. Here is my conversation with him: on violence and trauma in tech on and offline, and how social workers could help; on deadly hip-hop beefs and “Internet Banging” (a term Patton coined); hiring formerly gang-involved youth as “domain experts” to improve AI; how to think about the likely growing phenomenon of white supremacists live-streaming barbaric acts; and on the economics of inclusion across tech.
Greg Epstein: How did you end up working in both social work and tech?
Desmond Patton: At the heart of my work is an interest in root causes of community-based violence, so I’ve always identified as a social worker that does violence-based research. [At the University of Chicago] my dissertation focused on how young African American men navigated violence in their community on the west side of the city while remaining active in their school environment.
[From that work] I learned more about the role of social media in their lives. This was around 2011, 2012, and one of the things that kept coming through in interviews with these young men was how social media was an important tool for navigating both safe and unsafe locations, but also an environment that allowed them to project a multitude of selves. To be a school self, to be a community self, to be who they really wanted to be, to try out new identities.



